- Your Experience
- How old were you when the cyber bullying started?
- How did the comments make you feel?
- How did you over come this experience?
- In your opinion, what are the most common sites on which cyber bullying is popular?
- What advice do you have for other people who are going through this experience?
- What do you think can OR should be done, to put an end to cyber-bullying?
This Agreement is made as of the date indicated below between Filmmaker (defined below) and Performer
(defined below), as follows;
1. Interviewee agrees to render services as an on-camera performer in connection with the production of the
Video (defined below).
2. The term is in perpetuity, and the territory of the footage is worldwide.
3. Interviewee hereby grants to Filmmaker, its successors and assigns the right to use and display
Interviewee's likeness and performance as contained within the Video for any and all purposes and in any
and all media channels, now known or hereafter devised.
4. I hereby release Filmmaker, its successors and assigns from any and all claims, demands and liabilities of
any kind or nature whatsoever arising out of the aforementioned materials and the use thereof.
5. Filmmaker, its successors and assigns shall be the absolute owners of any and all photographs, film,
Video and other materials (and all rights therein, including the copyright) produced pursuant to this
release. Interviewee further agrees, subject to the provisions above, that Filmmaker may use Interviewee's
photograph, and/or likeness in any manner and with whatever copy they choose. Interviewee understands
that Filmmaker is not obligated to use Performer’s image.
6. Interviewee represents that by signing this Agreement and Release, Interviewee fully intends to be legally
bound to the terms stated within or, if Interviewee is under the age of 18 years, this Agreement and
Release is being signed by Interviewee's parent or legal guardian who represents his/her agreement to the
terms stated within and that Performer will be legally bound to such terms.
7. Interviewee's acknowledges that the production is non-union and holds the Filmmaker harmless for any
claims relating to hiring the Interviewee on that basis.
Date: ___13/12/13________________________________
Signature of Performer/Guardian ___________________________________
Print Name of Performer/Guardian ___________________________________
Character/Role __Sam Johnson_- Interviewee________________________________
Performer’s Email & Physical Address ___________________________________
Payment Amount (if applicable) ___________________________________
Signature of Filmmaker ___________________________________
Print Name of Filmmaker _____TRC News Media______________________________
Title of Video _TRC News Package__________________________________
Presenter outlines and gives information about cyber bullying - David outside of school with children walking into school in the background. Finishing with some establishing shots of the school.
Facebook conversation of cyber bullying taking place with voice over- Visual Facebook conversation with a live cyber bullying conversation taking place.
Statistics about cyber bullying- Picture freezes and then shows several facts about cyber bullying.
Interview with victim of cyber bullying- Questions about their experiences and feelings when they were being bullied through the internet.
Live scene presenter briefly talking about the hacking incident which took place- introduces the hacking story, talks briefly about it outside the scene of the crime.
Footage of Akshays room with the hackers work area- Quick short shots of the areas the work spaces the hacker used.
Finish with presenter talking about punishments and wraps up the new story.
Props:
- Crime tape for the second story to place around the house.
- Computer, Keyboard and Mouse for both stories.
- Microphone for both presenters of each stories.
Equipment:
- High quality camera to ensure that the footage we film is to a high standard.
- Tripod which helps keep the camera steady and gives a good finish to shots.
- Microphone for both presenters in each story to ensure that what is being said can be heard clearly.
Costumes:
- Each presenter preferable would wear black trousers/jeans, black shoes, white shirt and a black blazer/jacket.
- Dark clothing for the interviewee to match the dark and dimmed background to hide their identity.
Click on photo to enlarge
Our interviewee replied promptly and this helped us to keep organised and progress with our package.
One example that I found very useful was from the website: http://webcache.googleusercontent.com/search?q=cache:WAW9xsfo410J:www.essexinsurancebrokers.com/content/Film%2520Production%2520Risk%2520Assessment%2520Form.doc+risk+assessment+form+filming&cd=1&hl=en&ct=clnk&gl=uk
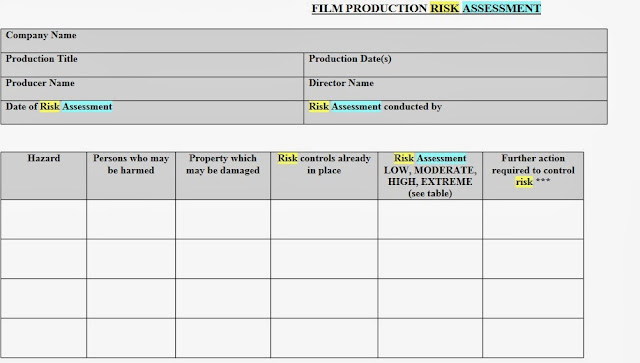
This risk assessment template was very helpful as it shows a clear table of how the risk assessment form should be set up, and the important pieces of information than needed to be included and by looking at this it enabled me to create a my own template for our risk assessment form. Here is what my form looks like:
50% of people who took this survey were female. This shows that our News package could be suitable and relatable to both genders.
100% of people who took this survey are between the ages of 17-19 years old, this doesn't decrease our target audience but makes us more aware of what age group are most interested.


Available hours - 1pm - 9pm
Location Fee - None
Power - n/a
Windows - Big windows in small room, can be covered by blinds
Security - Secure alarm system
Access - Give people directions via MapQuest, plus email them directions of where to go once they drive through town.
Police/Hospital - Approximately within 3 kilometres
Transportation - Participants can reach location public transport via 113, 186, 288
Then after we watched this we discussed what ideas we could take from this and how we could implement it, in a unique style for our news package.
What did we learn from this?
When looking at this professional graphics news piece from Channel 4 News we learnt and found many different creative aspects which we would like to implement in our piece, however in our own different style. Some of these were:
-Effective Title Transitions
- Typography Text Effects
- 3D Animation
- Animation of Still Images.
- Transitions which link to the clip theme. (For example an explosion occurs, have an explosion vfx come in).
Our task was to copy this 8 Shot Short News Package:
And here is what we produced as a group, i felt after some feedback we really looked closely at the original and tried to imitate it as closely as we can.
Here is our version of and 8 shot short news package enjoy!
Individually, we analysed and made a list of useful rules and tips that we had gained from the: .
We then discussed our views and notes and have come up with the following shortened list if five rules of creating a professional news package:
To get as involved in our blog as possible visit our survey and help us by giving constructive feedback to aid our news package. To do this visit our survey at SurveyMonkey, please click this link below to proceed:
Click here to take survey
Contact us at: trcnewsmedia@gmail.com
johnsileo, you will see that the name is used to send business to a gentleman who is also an identity theft speaker. The actual account is @john_sileo. Whether this is considered social networking squatting or social networking identity theft, it’s impersonation.http://prezi.com/9hsjpjxyaksr/technological/
This is an article from the BBC, written by Rory Cellan-Jones, Technology Correspondent.
Leading search engine companies By Google and Microsoft have agreed measures to make it harder to find child abuse images online.
As many as 100,000 search terms will now return no results that find illegal material, and will trigger warnings that child abuse imagery is illegal.
PM David Cameron has welcomed the move but said it must be delivered or he would bring forward new legislation.
Child protection experts have warned most images are on hidden networks.
In July, Mr Cameron called on Google and Microsoft's Bing - which together account for 95% of search traffic - to do more to prevent people getting access to illegal images.
He said that they needed to ensure that searches which were unambiguously aimed at finding illegal images should return no results.
New software
Now both companies have introduced new algorithms [software instructions] that will prevent searches for child abuse imagery delivering results that could lead to such material.
Writing in the Daily Mail, Google executive chairman Eric Schmidt says: "These changes have cleaned up the results for over 100,000 queries that might be related to the sexual abuse of kids."
"As important, we will soon roll out these changes in more than 150 languages, so the impact will be truly global."
The restrictions will be launched in the UK first, before being expanded to 158 other languages in the next six months.
Mr Schmidt goes on to describe work in the area of deterrence. "We're now showing warnings - from both Google and charities - at the top of our search results for more than 13,000 queries."
Alert warning
Warnings like this will appear on screen if users type in search terms related to child abuse
"These alerts make clear that child sexual abuse is illegal and offer advice on where to get help."
Microsoft, which in a rare display of unity is working closely with Google on this issue, says its Bing search engine will also produce clean results.
The company said it had always had a zero tolerance attitude to child sexual abuse content and had been putting in place stronger processes to prevent access since the summer.
Later on Monday, the two companies will join other internet firms at Downing Street for an Internet Safety Summit.
The prime minister said significant progress has been made since his speech in July calling for action, but warned that new legislation could be introduced if the companies failed to deliver.
At the time, he said that Google and Microsoft had said that blocking search results couldn't be done but he did not accept that.
Tory MP Claire Perry, Mr Cameron's adviser on the sexualisation and commercialisation of childhood, told BBC Radio 4's Today programme the new measures were a "great step forward".
"We're not declaring victory but this is a massive step in the right direction," she said.
'Missed opportunity'
But Jim Gamble, former head of the Child Exploitation and Online Protection Centre (Ceop) told BBC Breakfast he did not think the measures would make any difference with regard to protecting children from paedophiles.
"They don't go on to Google to search for images. They go on to the dark corners of the internet on peer-to-peer websites," he said.
He said search engines had already been blocking inappropriate content and the latest move was just an enhancement of what was already happening.
A better solution would be to spend £1.5m on hiring 12 child protection experts and 12 co-ordinators in each of the police regions to hunt down online predators, he added.
NSPCC chief executive officer Peter Wanless said "a concerted and sustained effort from all quarters" was needed to stay one step ahead of sex offenders that were getting ever more technologically advanced.
"This is the key child protection issue of a generation - we cannot fail," he said.
A June report by the Ceop highlighted how the "hidden internet" helped distributors of child abuse images to evade detection by using encrypted networks and other secure methods.
Google and Microsoft have agreed to work with the UK's National Crime Agency and the Internet Watch Foundation to try to tackle networks which host child abuse images.
The two companies are also using their technological expertise to help in the identification of abuse images.
Microsoft's PhotoDNA already allows a photo to be given a unique "fingerprint" which means it can be tracked as it is shared across the internet. Now Google has developed VideoID which does the same job with videos.
Both firms will provide this technology to the National Crime Agency and other organisations to help in the work of finding and detecting those behind the creating and sharing of child abuse images.
But critics have accused the government of underfunding online child protection.
Ceop, which is now part of the National Crime Agency, has been accused of missing a recent opportunity to identify hundreds of people downloading illegal images.
Police in Toronto revealed that in 2012 they had shared hundreds of names of British people with Ceop who were alleged to be customers of a Canadian firm that sold videos of young children.
The operation to close down the business saw hundreds of people arrested in Canada and around the world - but none in Britain.
On Friday, the National Crime Agency said Ceop had examined the material but it had been classified as being on a low level of seriousness. However, the agency has now ordered a review of Ceop's handling of the case.
http://www.bbc.co.uk/news/uk-24980765
The letter
Surveys about Cyber Bullying:
http://www.ditchthelabel.org/annual-cyber-bullying-survey-cyber-bullying-statistics/
Pedophiliac: http://www.channel4.com/news/should-you-let-your-child-play-in-habbo-hotel
Adults log onto teenage social networking sites Like Habbo Hotel etc and inappropriately speak to underage persons. The link above shows an article about this topic specifically on Channel 4.
Hacking: A 26-year-old journalist has been charged with allegedly conspiring with members of the hacker group Anonymous to hack into the Tribune Co. TRBAA -0.51% system and alter a news story on the Los Angeles Times website, the Justice Department.
Situations like this are considered Technology related crime.
The first picture was more of like a journey and futuristic look due to the colours and also the actual animation of the texture.
We came up with a conclusion that instead of having real "outside public" pieces of footage, we should have online screenshots and speedclips of social network's and spying agencies such as MI6, SIS and finally found inspiration for two video clips called "AngelDust thriller" and "GeekNews".
MI6 - <a href="https://www.sis.gov.uk/"></a>
SIS - <a href="http://goo.gl/AlrVUB"></a>
Angel Dust - <a href="http://goo.gl/7nzIiQ"></a>
Geek News - <a href="http://goo.gl/AR0gDY"></a>
What was the Silk Road?
Total Pageviews
Blog Archive
-
▼
2013
(53)
-
▼
December
(15)
- Interview Questions
- 3 Column Script (Antonio)
- Release form for interview subjects (David)
- Structure For Our News Package (Antonio)
- List of Props, Equipment & Costumes If Necessary (...
- News Package Storyboard (AKSHAY)
- Contact with interview subjects (David)
- Call Sheet (Antonio)
- Group Skype call (David)
- Group Skype Call (AKSHAY)
- Risk Assessment Form And Checklist (Antonio)
- Survey Analysis (David)
- Media Lesson: 05/12/13 (J.)
- Location Profile (David)
- Storyboard Process (AKSHAY)
-
►
November
(22)
- Graphics Planning (AKSHAY)
- 8 Shot Short News Package (AKSHAY)
- 18/11/2013 Lesson
- 8 Shot Short News Package (Antonio)
- Producing a TV News Package
- Planning A TV News Package Video (AKSHAY)
- TRC Survey (David)
- Feedback Report (Antonio)
- Progression Of Music (Antonio)
- TV news package part 2.0 15/11/13 (David)
- NEW Blog Design (AKSHAY)
- TV News Package Story Idea (Antonio)
- Police Warn of 'Ransom' Spam - J.
- TRC NEWS Opening Sequence (AKSHAY)
- Opening Sequence FULL Creation/Editing Process (AK...
- UK Police Launch Campaign to Shut Down Torrent Sit...
- TV News Package Story Idea (David)
- Opening Sequence Texture Ideas (AKSHAY)
- Padlet Wall (Antonio)
- News Package & Opening Sequence Discussion (AKSHAY)
- News Package and Development (David)
- TRC News - LOGO PLANNING - Hand Drawn Designs (AKS...
-
►
October
(16)
- Key Framing Animation Of A Football (Antonio)
- TRC News - Production Location Risk Assesment Form...
- David's Keyframe Animation (David)
- Keyframe Animating TRC News Logo Task (AKSHAY)
- Todays Lesson 11/10/2013 (Antonio)
- TRC NEWS Logo Analysis (AKSHAY)
- Updated News Intro Analysis Prezi (David)
- TRC News - Akshay Opening Introduction (AKSHAY)
- Police ‘overwhelmed’ by Internet-related crime, (D...
- (J.) UK men arrested over Silk Road links - BBC Ar...
-
▼
December
(15)
















.jpg)
.jpg)

















